ASSURANT™ Suite
With the ASSURANT™ Suite of software tools, you will feel secure knowing your cyber vulnerabilities have been addressed and you have the documentation to prove it.
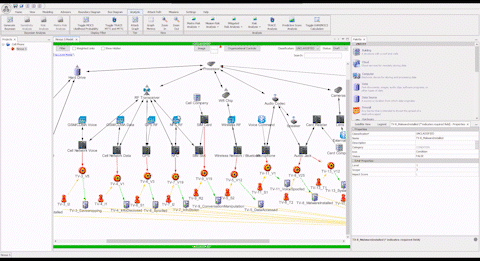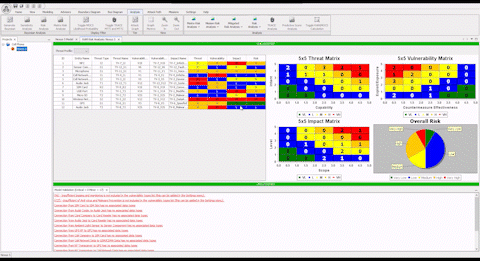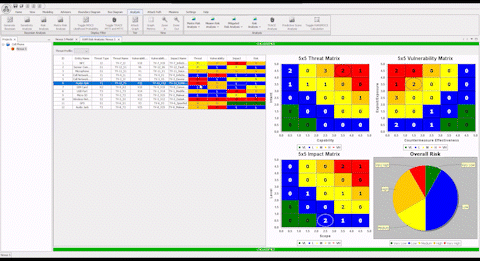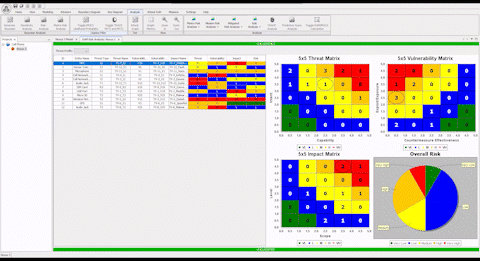
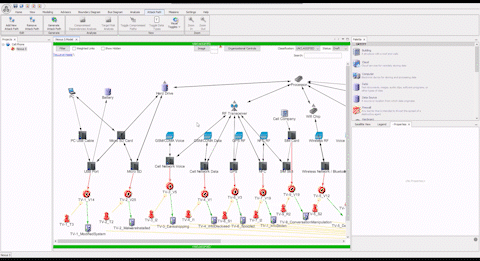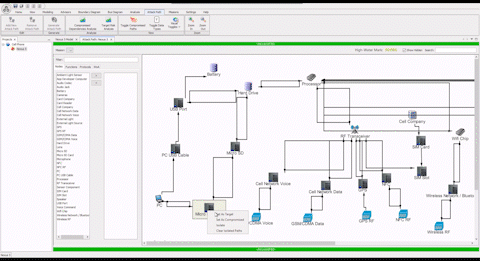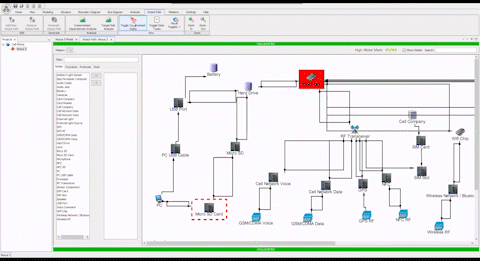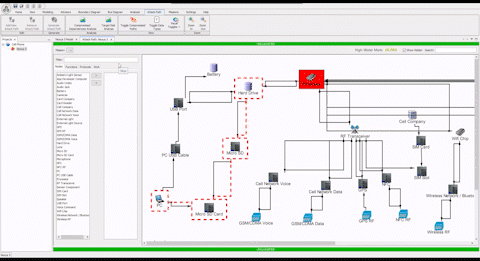
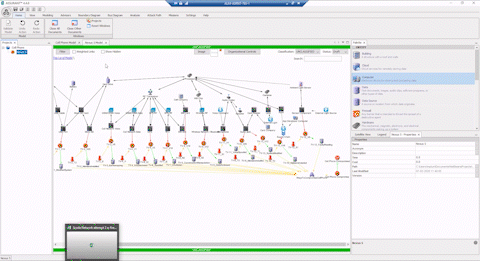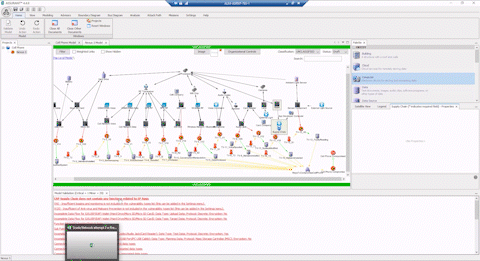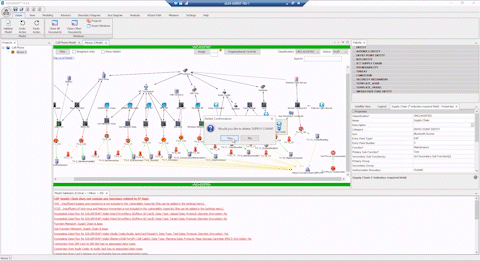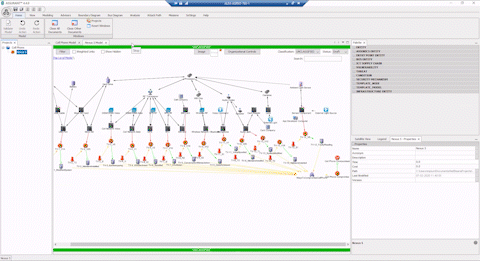
Comprehensive Cyber Security is Complex
4,000+ ASSURANT™ Users
10,000+ Systems/sub-systems analyzed
100,000+ Manhours saved
What Our Clients Say
“This system allowed me to identify missing components when the model validation engine ran. These were components which had infrequent changes and therefore were not commonly documented. The ASSURANT™ model told us that there were some elements missing. When we compared our sources against the model result, we discovered existing legacy components which had previously lacked documentation. The addition of these components to the model has given us confidence in the model’s completeness and improved our cyber readiness.”

Cyber Model Engineer
“Without the ASSURANT™ attack path analysis visual capability, it’s difficult to explain the complexities of a cyber battlespace to non-experts, and us good guys in the fight are often only learning from our mistakes in the wake of a cyber-attack. The different ways to visualize attack paths allows time to get ahead of the tactics and techniques of cyber actors by allowing us to simulate “black hat” scenarios for when a network artifact becomes compromised.”

Attack Path Analyst
Contact Us
1408 University Dr
College Station, TX 77840
(979) 814-4348
[email protected]
Resources
Identify and Prioritize Your Business Cyber Risks with ASSURANT®
Export Warning. The Software might be described by items on the U.S. Munitions List (title 22, part 121, of the Code of Federal Regulations), including in Category XI and Category XXI.