The role of cyber survivability in the business enterprise.
Cyber attacks damage your reputation. Recovering from cyber attacks takes money and resources. Countering cyber attacks requires specialized personnel with supporting technical and organizational overhead. Foreseeing and preparing for cyber attacks is challenging. Cyber attacks disrupt business operations. The threat of cyber attacks is a constant drain on enterprise resources and attention. In short, the threat of cyber attacks is a threat to the survivability of the enterprise.
Cyber security is a field of study and application that attempts to identify and mitigate cyber attacks. Cyber security is a burgeoning industry; the marketplace is awash with cyber-security methods and tools. But cyber security, as practiced in the current state of the art, is reactive in nature. Current approaches rely heavily on regulation and compliance reporting – palliatives, at best.
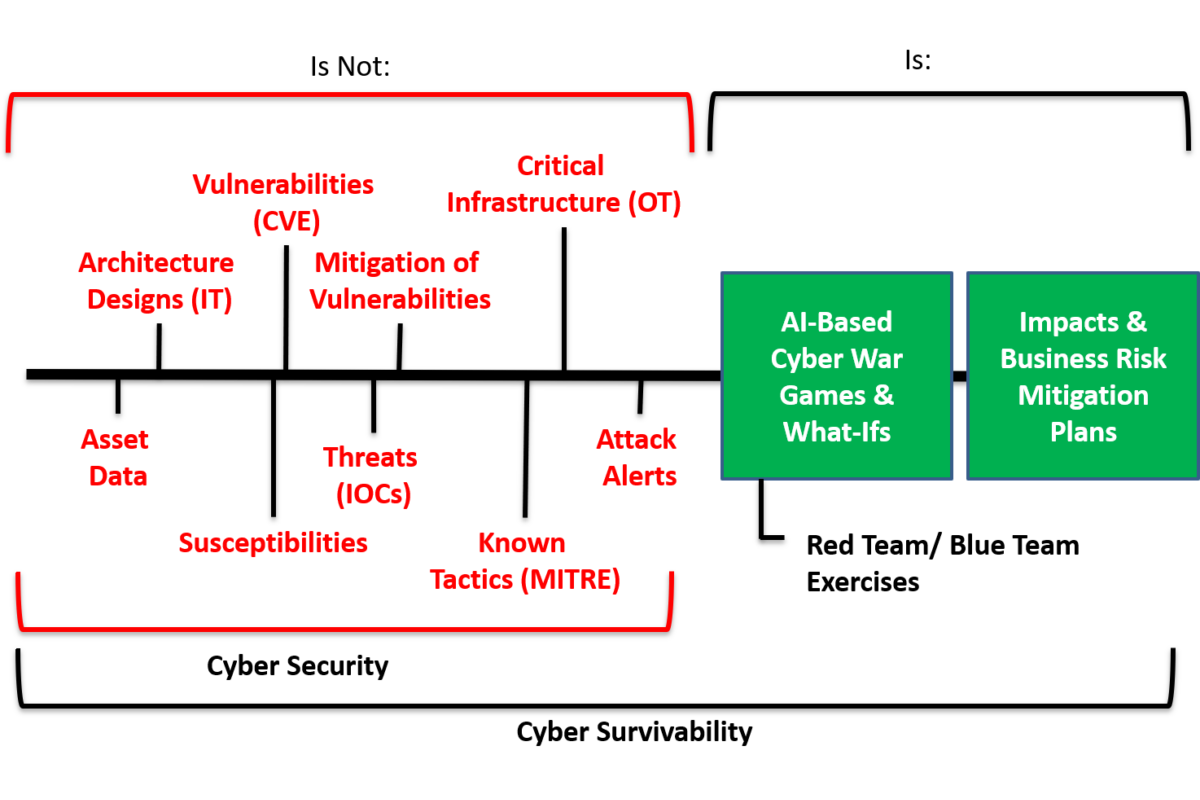
Cyber survivability builds on cyber security to address business impacts — safety, finance, reputation, business continuity, environmental impact, fiduciary, and legal. Cyber survivability combines the reactive nature of cyber security solutions with a proactive concern about the potential for losses and an operational focus on visibility and actionability. A cyber survivability solution evaluates and analyzes potential attack paths using a digital twin of your cyber infrastructure. Cyber survivability protects your business, not just your IT assets!
As CIOs and IT security officers can attest, the presence of a cyber vulnerability does not mean there is a threat to the enterprise. Similarly, regulatory compliance does not mean security. Vulnerability databases are based on the weaknesses that have already been exploited; compliance checklists respond to those experiences. The presence of some vulnerabilities will lead to business risk, but many – indeed, perhaps most – vulnerabilities do not represent a business risk in any particular enterprise. Addressing every vulnerability — checking every compliance list box — is expensive. Enterprises typically realize superior benefits from focused, intensive intervention and remediation aimed at shoring up the business itself.
The challenge, of course, is knowing which vulnerabilities represent business risks. A responsible defense against those risks requires an assessment of the potential for damage and an understanding of the cost and effectiveness of available mitigations. Dealing with these threats at an operational level requires a compressive picture of the enterprise at risk and constant awareness of the evolving cyber threat environment.
So, what is Cyber Survivability, and how is it different from cyber security? How does it expand your current perimeter threat detection or Endpoint Detection and Response (EDR)?
Cyber Survivability is focused on business risk; it builds on cyber security to protect all aspects of your enterprise. For example, a vulnerability is not a business threat unless:
There is a weakness or flaw in your system; an adversary has the capability to exploit that weakness; and that adversary has the opportunity to exploit that weakness.
Capabilities that support cyber survivability allow system managers and stakeholders to test changing mitigations and attack vectors. Managers and stakeholders are able to assign costs to mitigations and work in coordination with existing cyber security platforms already in use.
Cyber survivability analysis must:
- capture a complete description of your system;
- aid users in the identification of the flaws, weaknesses, or susceptibilities that exist;
- identify potential impacts on the system of exploiting a vulnerability and how that exploit could propagate through the system’s connectivity network; and
- assist cyber security efforts by quantifying risks, planning mitigations, and training personnel.
New susceptibilities, vulnerabilities, and threats are emerging at a rapidly increasing rate. Because the odds that your system will be the first victim of attack are statistically low, you must maintain a heightened situation awareness of your infrastructure and its environment. A cyber survivability capability needs to use advanced algorithms, such as artificial intelligence (AI), to keep abreast of the rapidly evolving cyber security environment.
Cyber-survivability support requires access to Natural Language Processing (NLP) technologies that can scan open-source reference materials and evaluate national and private vulnerability and attack databases. Understanding this constant flood of new information requires a more effective user experience, especially when interacting with text-based source materials available in the CVE, CWE, NVD, and MITRE ATT&CK data sets.
When a threat appears — albeit from an adversary, an insider, or an environmental event – the survivability system should identify any potential business impact and the way that impact could be propagated through the system’s connectivity network. The result should be an assessment of overall impact; an assessment of impact on the business.
Advanced algorithms – AI technology – can be used to support cyber security and investment decisions. The system should be able to generate predictive vulnerability and risk scoring for arbitrary IT configurations, weight attack paths and node susceptibility, and recommend optimal investment strategies to achieve risk mitigation. Using this analysis, risks can be quantified, mitigations can be planned, and personnel can be trained.
In summary, a cyber survivability system describes your complete system, identifies any flaws, evaluates an adversary’s ability to exploit those flaws, projects the impact of an attack, identifies the best mitigations, quantifies costs and losses to the business, and assists in generating supporting documentation.