The ASSURANT™ Suite
Reduce the cost of making your cyber system secure and have the documentation to prove it.
ASSURANT™
A suite of cyber-focused tools and services that allow you to model, visualize, analyze and report on cyber physical systems in order to feel secure knowing that your cyber vulnerabilities and business risks have been addressed and you can generate the documentation to prove it.
What Does ASSURANT™ Do?
Model
Model
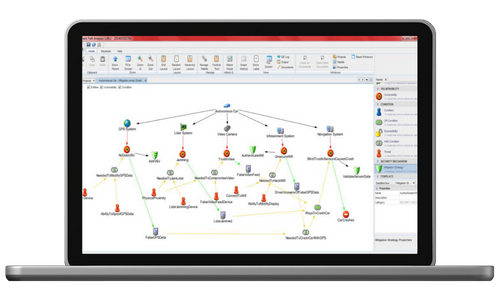
ASSURANT™ provides an intuitive, drag-and-drop, topological modeling capability in which you model your cyber-physical system – down to the component and bus level. The model can be annotated with key parameters necessary to identify and assess cyber vulnerability.
Visualize
Visualize
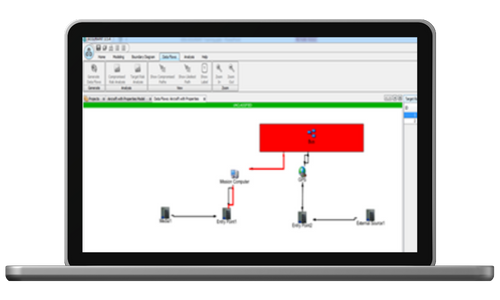
A flexible graphical presentation of the cyber-physical system model promotes common understanding of your system and rapid identification of cyber-security issues and opportunities.Analyze
Analyze
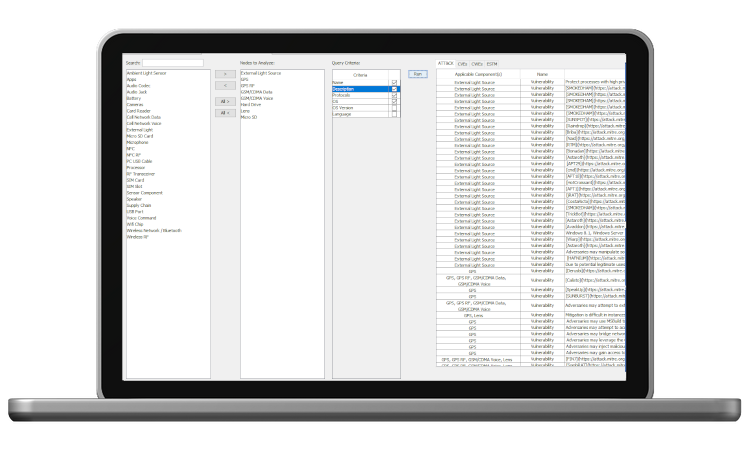
ASSURANT™ can make use of existing threat and vulnerability databases, such as the Common Vulnerabilities and Exposures (CVE) dataset, to identify potential vulnerabilities in your system; can identify and evaluate attack paths; and can calculate risk scores using several common techniques.
Report
Report
ASSURANT™ contains a template-based report generation capability that can generate reports supporting cybersecurity risk assessment (CRA) and can support many common compliance reporting requirements, such as Government Authority to Operate (ATO) documentation.